Passkey Technology: How Do Passkeys Work?
Passkeys are a new way of signing in to your online accounts with a biometric sensor or PIN, eliminating the need for passwords. They are predicted to dethrone passwords as the most popular form of identity verification in the coming years.
Here's a top-level analogy for how passkeys work: imagine a super secure keycard for each website or app, stored on your phone. That's kind of like a passkey. It uses your fingerprint or PIN to verify it's you, then proves it to the website without ever revealing the actual key. Websites can't steal it like a password, and you don't need to remember anything!
Passkeys can be hard to wrap your head around. There's a good bit of magic happening behind the scenes that goes beyond the scope of this article. In the Technical Overview section, I've linked to several resources that will help you understand passkeys from an implementation perspective.
Table of Contents
What Is Passkey Technology?
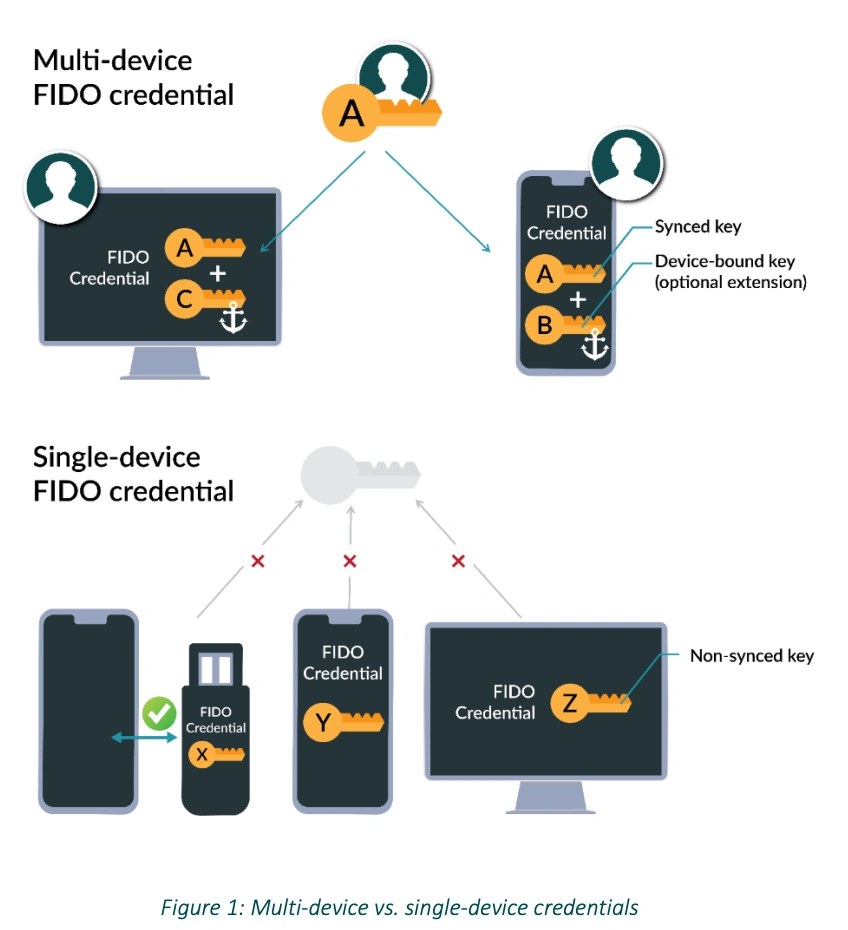
Multi-device FIDO credentials, commonly known and advertised as passkeys, had their earliest iterations decades ago as hardware security keys like smart cards. These hardware solutions required specialized readers and were expensive to deploy and maintain, and never achieved ubiquity in consumer security.
In 2015, the FIDO Alliance, a group of industry leaders whose goal is to "help reduce the world’s over-reliance on passwords," developed and published a set of specifications for phishing-resistant authentication mechanisms. By 2020, most browsers had implemented the WebAuthn specification, which eliminated the need for special hardware and paved the way for relying parties (websites/applications) and platform vendors like Apple and Google to bring passkey technology to the average consumer.
With Apple syncing your passkeys through its iCloud Keychain and Google doing the same with its password manager, and with passkey storage/syncing just around the corner for third-party password managers, the last roadblock for passkeys is being eliminated.
You can now use the biometric or PIN that unlocks your phone to sign in to any compatible website. Your passkeys cannot be phished, guessed, or brute-forced - a threat actor would need both your physical device and the PIN or biometrics to unlock it.
How Passkeys Work: A Technical Overview
Passkeys leverage the power of public key cryptography and secure key storage on devices to provide a more robust and user-friendly authentication experience compared to traditional passwords.
Underlying Standards
Passkeys rely on two key specifications:
- WebAuthn (Web Authentication): This defines how browsers and websites interact for secure authentication. It allows websites to request credentials (passkeys in this case) from the user's device and validate them.
- FIDO2 (Fast Identity Online 2): This is a broader set of standards developed by the FIDO Alliance for strong authentication. It includes CTAP (Client to Authenticator Protocol), which defines how devices (like phones) communicate with authentication hardware (security keys) or software (built-in authenticators).
Passkey Creation
When you create a passkey, here's what happens behind the scenes:
- Public-Key Pair Generation: Your device generates a public-key cryptography pair. The public key is sent to the service and stored on their server. The private key remains securely stored on your device, often in a trusted platform module (TPM) or secure enclave.
- Attestation Ceremony: To ensure the private key is generated securely by your device and not malware, an attestation ceremony takes place. This involves the device proving to the service (often with the help of the platform like Android or iOS) that it can securely generate and manage cryptographic keys.
Passkey Login
Logging in with a passkey involves:
- Challenge: The service sends a random challenge to your device.
- Signed Response: Your device uses the private key to decrypt the challenge and create a digital signature. This signature proves you possess the private key without revealing the key itself.
- Public Key Verification: The service retrieves the public key it has stored for you and uses it to verify the signature in the response. If valid, it grants you access.
Additional Security Features:
- FIDO2 extensions can be used for features like resident credentials (passkeys stored only on your device) and multi-device support (using your phone to unlock passkeys on your computer).
- Biometric Authentication: You can use your fingerprint, PIN, or facial recognition to unlock the private key on your device, adding an extra layer of security.
Unless I were to turn this blog into a treatise on public key cryptography, device security (such as Trusted Execution Environments), and the history of Authentication in general, I can't give a complete technical explanation of passkeys. If you wish to understand passkeys at that depth, you may be better served by perusing the FIDO Alliance library of whitepapers here.
In this excellent review of passkeys by Vittoria Bertocci, we learn how the FIDO2 specification allows passkey implementation: "...by using the Javascript API defined in the WebAuthn specification, developers can leverage either hardware keys (e.g., YubiKeys) or secure hardware on the device (e.g., secure elements on your phone, TPMs on your laptop) gated by biometric sensors to authenticate users without using passwords."
Additionally, Apple's 15-minute video introducing passkeys for developers explains important concepts - you can watch the full video or read the transcript.
Credit: FIDO Alliance whitepaper on multi-device FIDO credentials
Passkey Login Examples
Note: Below is just one example of creating and logging in with passkeys. The process looks different depending on the website/application you're signing in to, the device you're signing in from, and whether or not you use one platform vendor's ecosystem or several (Google, Microsoft, Apple etc).
For this example, I'm using the demo at https://www.passkeys.io/.
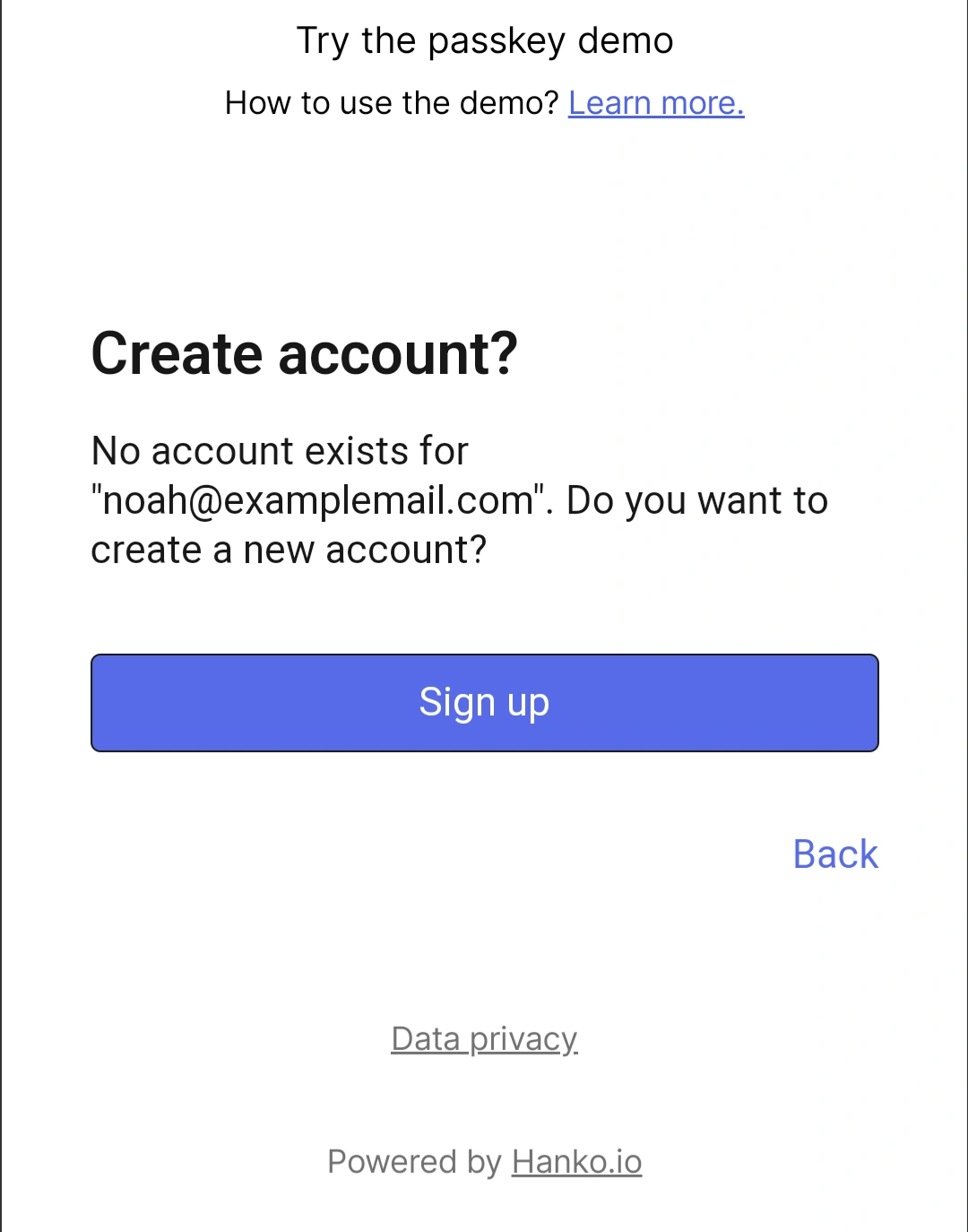
First, I'm signing up on a Pixel 4A running Android 13.
Since it's my first time logging in, I'm asked to create an account using my email address.
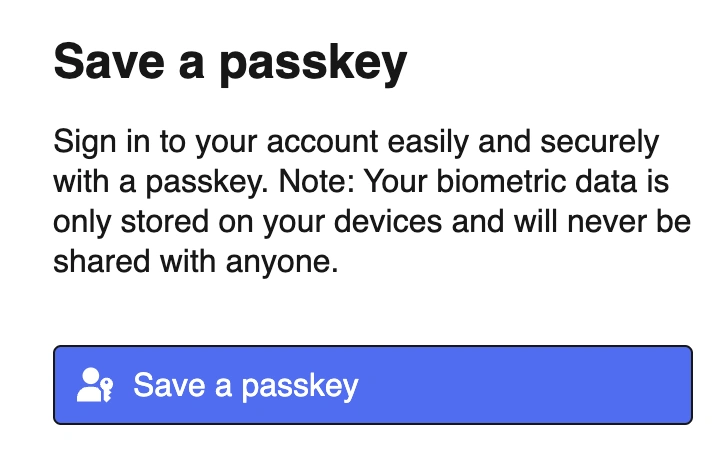
Next, I'm asked to save a passkey.
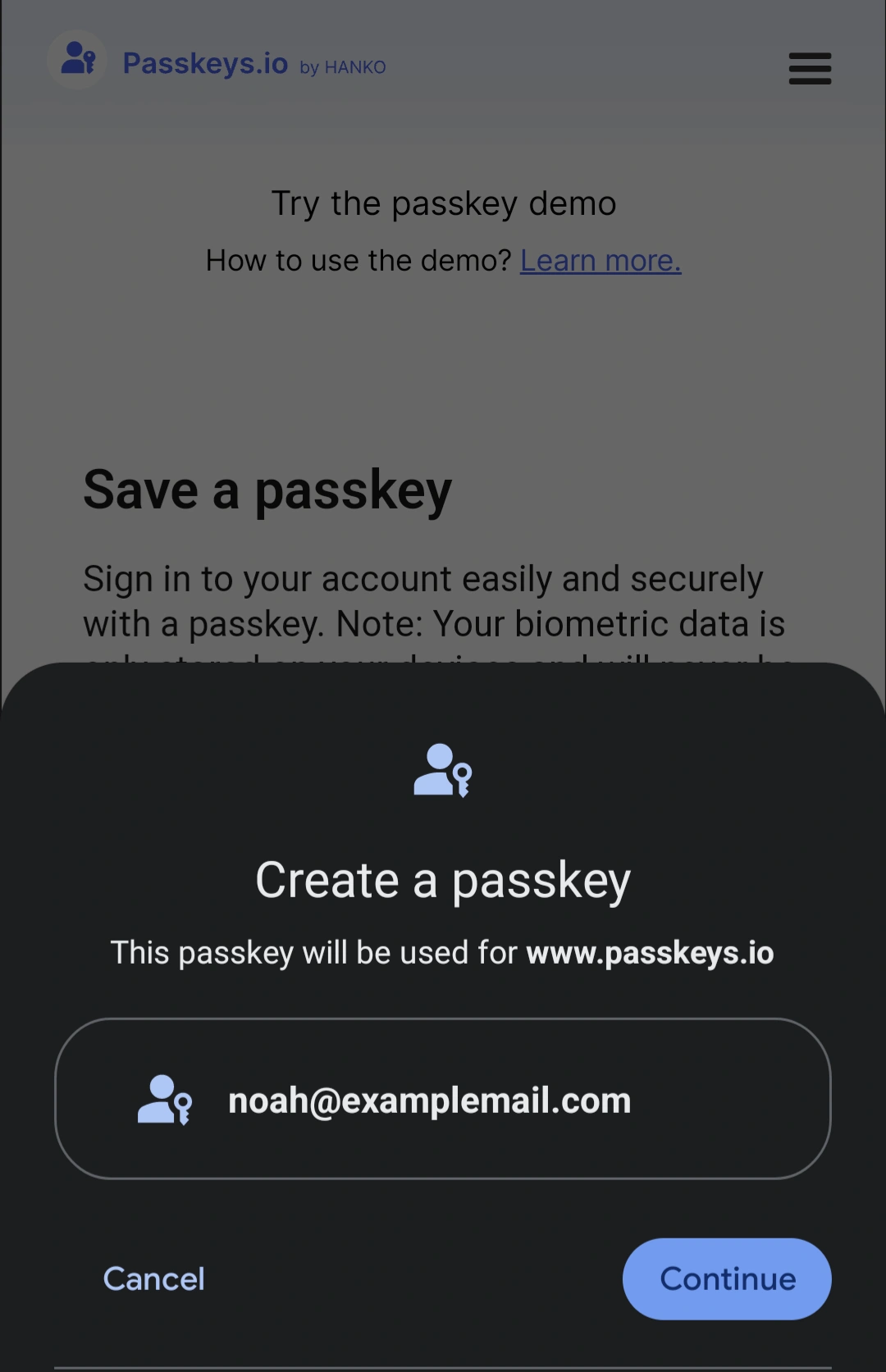
By tapping "Save a passkey," I prompt my device to display its own popup confirming that I really want to save a passkey. This popup looks different depending on your platform vendor (Macbook, Android smartphone, etc.).
Tapping continue displays a prompt to confirm passkey creation by unlocking my device with my fingerprint or PIN. Doing so authorizes the creation of a public/private cryptographic key pair. The private key is stored on your device, and the public key is stored by the relying party - in this case, passkeys.io.
I touch my fingerprint sensor and am instantly logged into passkeys.io. Account setup is complete.
The device on which I created the private key will now take care of roaming - more on that in a moment.
That's it!
Well - not quite.
It's pretty sweet that I didn't have to create, remember, or save a password. The trade-off is that I've only authorized this specific device to sign in to this account - or, if syncing is enabled, other Android devices synced to the same Google account.
Now, I need to log in on my Macbook.
- On the passkeys.io homepage, I select "Sign in with a passkey."
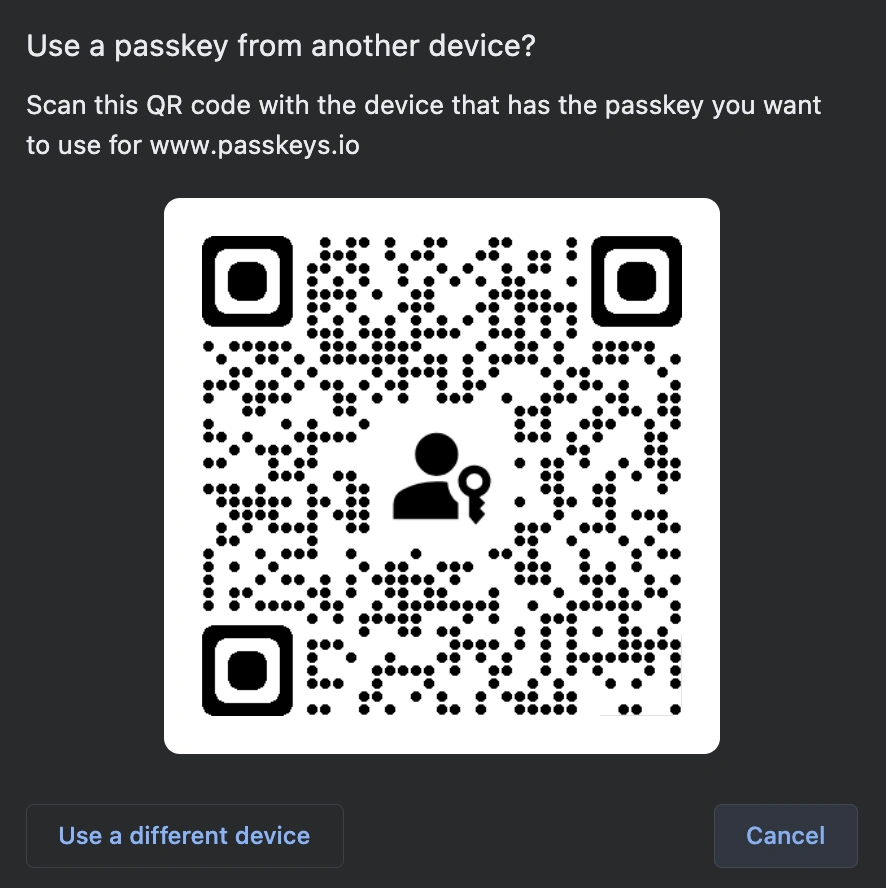
- Selecting "Use a different phone or tablet" displays a QR code (if Bluetooth isn't on, your devices will ask permission to turn it on).
- I scan the QR code with my phone.
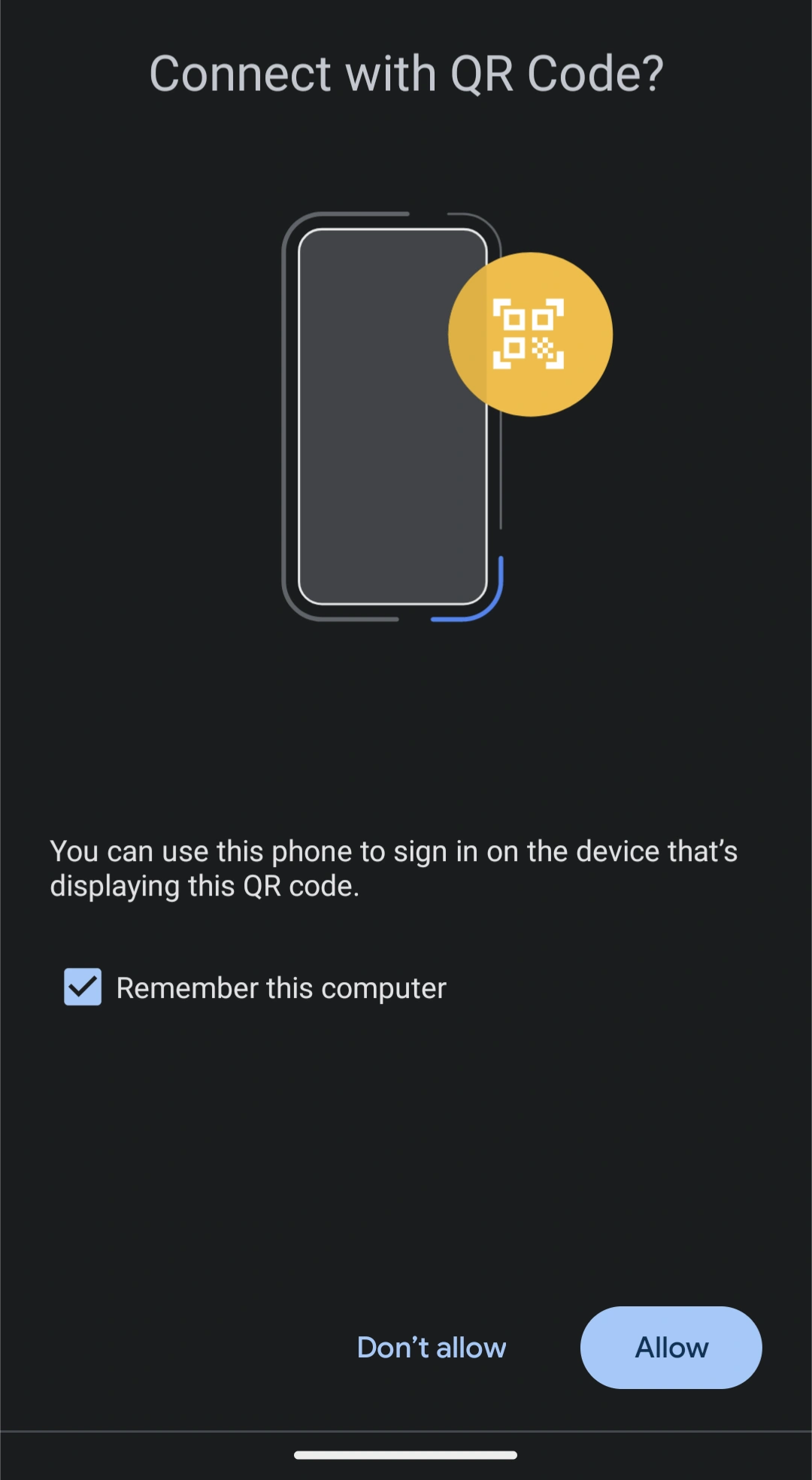
- This initiates a Bluetooth handshake.
Note: The passkey authentication ceremony is not done over Bluetooth. Bluetooth is used to confirm that the devices are geographically near each other. This thwarts remote phishing attempts and a host of other remote attacks.
- Once this virtual handshake has taken place and the devices agree that they're close to one another, they go to an authorized verification server to authorize the new device.
Note: The private key on device 1 (Android smartphone, in my case) is not transferred to device 2 (Macbook). Device 1 has simply confirmed that device 2 is in close proximity and performs a passkey authentication ceremony to allow device 2 to log in.
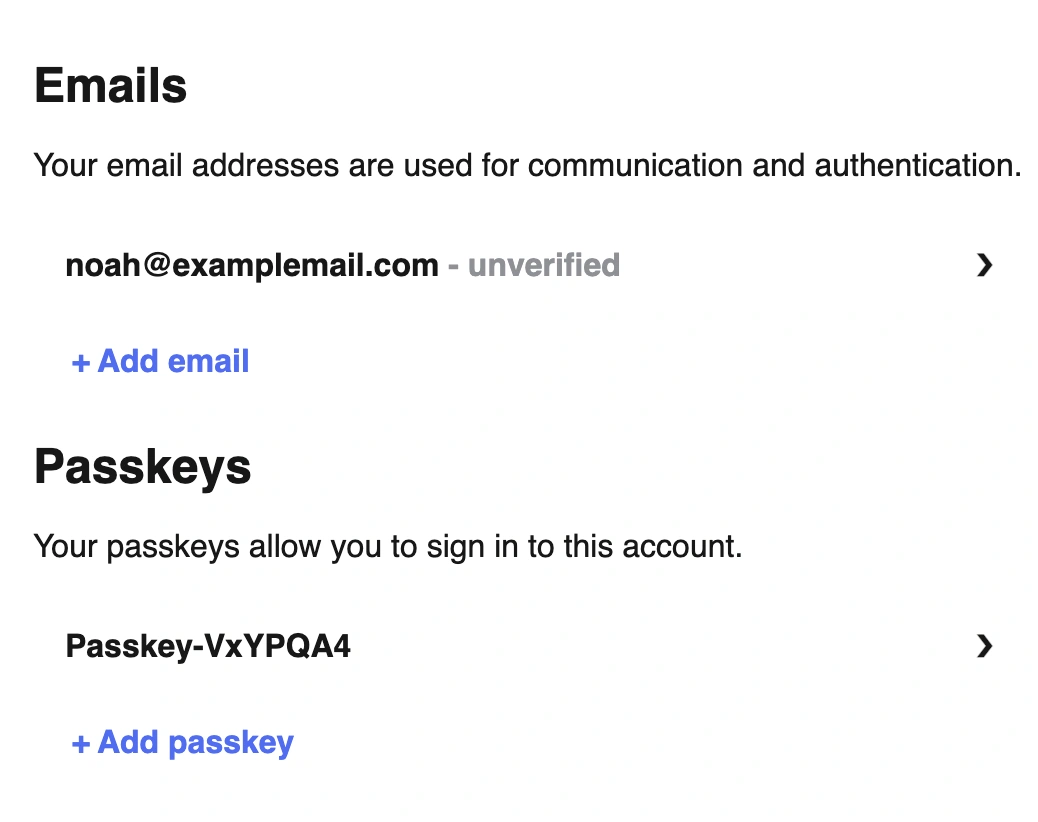
- Optimally, the website would automatically ask if I want to create a passkey for this new device - but it's up to the website (relying party). On passkeys.io, I need to click + Add a passkey to create a passkey on the Macbook so I can log in without my phone.
When I sign in to passkeys.io on my Macbook, I can now do so with my fingerprint or device password.
This screenshot drives home the point that passkey security = device security
If your device does not have a passkey and cannot set it up (or you choose not too), an alternative authentication method is provided such as a one-time code to your email. Security is then dependent on your email's security.
Lastly, I'd like to point out a side-effect of public-private cryptography. While you can delete your account on the website or application, this only deletes your public key. Your device doesn't know that its public key pair has been deleted, so when you sign in, you will be prompted to "Use saved passkey." However, selecting this option and verifying with your fingerprint causes the sign-in form to say, "This passkey cannot be used anymore." You need to delete your private keys separately.
Device-bound passkeys vs. synced passkeys
Apple and Google support syncing passkeys within their ecosystem. As you can read on Apple's memo here, this greatly increases convenience while placing the security of your private cryptographic key in Apple's hands.
If you don't want this, you can disable passkey syncing and use the alternative method of turning on Bluetooth to confirm proximity and authorizing a new device to create its own passkey, thus adding a new device to the list of those that can log into the given account.
Passkeys vs. Passwords: The Authentication Process
With passwords, anyone with your password can log into your account.*
With passkeys, anyone with your physical device and the ability to unlock that device (through PIN, pattern, or biometrics) can log in to your account.
Because the private key is device-based and invisible, phishing is impossible.
*Additional safeguards in the form of various Multi-factor Authentication technologies have been created to bolster the inherent weaknesses of passwords, but these also have their pitfalls.
How to Implement Passkey Technology
As a consumer, you are at the mercy of the website or application. Old devices may not support passkey technology. The app/website will recognize this and won't offer to create a passkey.
As Android 14 rolls out in September 2023, third-party password managers will be able to store and sync your passkeys.
Currently, Google Password Manager syncs passkeys between your Android devices that are signed into the same Google account.
For Apple, the iCloud Keychain takes care of syncing your passkeys.
With both ecosystems, syncing can be turned on and off.
Implementing passkey technology as a developer
- FIDO Alliance: The Fast Identity Online (FIDO) Alliance provides open standards for strong authentication. Their resources include specifications and guides for implementing passwordless and passkey-based authentication.
- Online Development Communities: Platforms like Stack Overflow, Reddit's r/programming, and GitHub discussions offer spaces for developers to ask questions, share experiences, and seek guidance on implementing passkey technology.
- FIDO 2 Specifications (including WebAuthn): A great page to get started learning the necessary specifications. Has a link to download the full specifications.
Implementing passkey technology requires a blend of understanding user needs, cryptography principles, and security best practices.
Boost Password Security With TeamPassword
Passkeys are not yet universally supported, so password security deserves your attention. If you share passwords with colleagues and need an easy, secure, and cost-effective way to do so, try TeamPassword. If you have questions, reach out to our support team - we're happy to hear from you.
TeamPassword focuses on frictionless implementation, ease of use, security, and exceptional customer support.
Need proof? Read what our customers are saying about us on G2.